Managed Assets: More Than Just Endpoints
Our comprehensive approach ensures all parts of your attack surface are continuously monitored and secured, reducing risk and strengthening your overall defense.
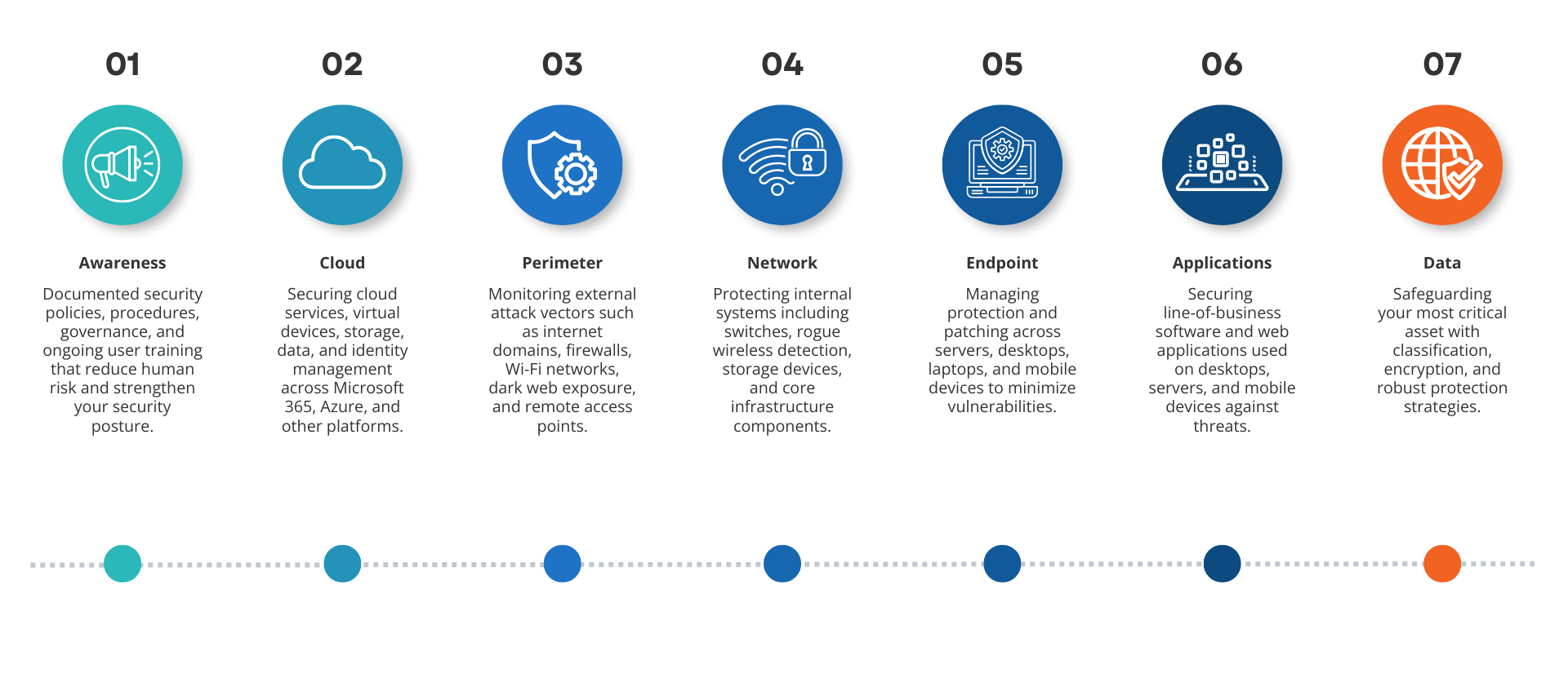
Our Proven Process
-
FIND
We identify vulnerabilities before attackers do—through deep assessments, threat detection, and continuous monitoring across your environment.
-
FIX
We quickly remediate risks with expert-driven solutions, patching gaps, hardening systems, and aligning your defenses with industry best practices.
-
FORTIFY
We strengthen your security posture long-term by implementing layered protections, automation, and awareness training—building resilience from the inside out.
Why Work With Us
-
We’re bounty hunters for threats, tracking and elminating risks.
-
Built for the real world with tested tools and proven methods.
-
From Microsoft 365 to every device in the field, you are secured.
-
Friendly experts, deeply invested in your success.
Related Resources
Cyber Safety Measures in the Remote Work Era
How to Build a Strong Security Culture for Leaders
Cybersecurity Challenges Resolved for Financial Institution
Other Services Worth A Look
Managed & Co-Managed IT
Full coverage or co-managed IT services that scale with your business.
Microsoft 365 Services
A secure Microsoft 365 environment designed for collaboration without complexity.
Azure Cloud Services
Move confidently with our Azure experts for secure, optimized performance.
Technology Review & Planning
Strategic IT planning services that align with your business vision.